Purge and Anonymization
The GDPR requires that personal data be kept in a form that permits identification of the data subjects for no longer than what is necessary for the purposes for which it is being processed.
This duration can be determined by law; otherwise, it should be determined for each phase of the datalife cycle.
At the end of the defined retention time, the data should be deleted or their identifying characteristics should be removed by means of an anonymization process.
#Objectives and issues
What is it about?
- The personal data deletion project aims at bringing applications and databases into compliance with the retention limitation principle.
- The purpose is to delete or anonymize the data at the end of the retention period determined and manage rules in the applications used for the automated deletion or anonymization of data at the end of the retention period.
What are the challenges?
- Since applications are interdependent, it is essential to map data flows, to analyze replication flows and the technical constraints of master applications, as well as the deletion capacity of existing applications.
#What is anonymization?
Anonymization consists in using a set of techniques to make it impossible to identify the person, in an irreversible way. It must no longer be possible to achieve:
- Individualization: is it always possible to isolate an individual?
- Correlation: is it always possible to link separate data sets about the same individual?
- Inference: can we infer information about an individual?
This technique is used for statistical purposes or when it is impossible to delete data.
There are two main approaches to anonymization:
Randomization
Randomization transforms the data so that it no longer refers to a real person.
- Adding noise to modify the data
- Permutation to mix the data
- Differential privacy
Generalization
Generalization allows data to be diluted so that it is no longer specific to one person but common to a set of individuals.
- K-anonymization or aggregation to group a data subject with k-individuals and thus prevent the possibility of isolating an individual.
- I-diversity / T-proximity to extend k-anonymity and ensure that it is no longer possible to obtain certain results through interference attacks.
#Our Approach
Why choose TNP Consultants?
Thanks to its technical and legal skills in data protection and digital transformation, TNP Consultants supports its clients in the definition and implementation of a personal data deletion strategy.
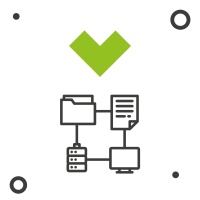
Data flow mapping, consideration of IT architecture constraints

Analysis of data usefulness for the company

Definition of the data strategy: anonymization, pseudonymization, deletion

Definition of roles and responsibilities

Implementation of the data strategy

Evaluation of individualization, correlation and inference risks

Documentation and project management



